华为usg6300防火墙如何通过命令如何设置上网,懂命令的人,对于防火墙出现故障会更好判断问题
发布时间:2024-04-06 文章来源:深度系统下载 浏览:
| 华为usg6300防火墙,通过命令如何配置上网,懂命令的人,对于防火墙出现故障会更好判断问题,防火墙基本的上网命令如何去配置? 下图所示:防火墙硬件设备。   防火墙各个面板名称作用。 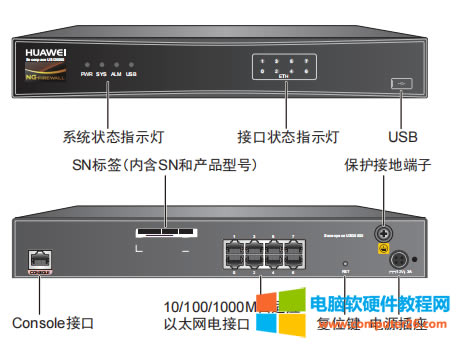 防火墙的基本连接拓扑图: 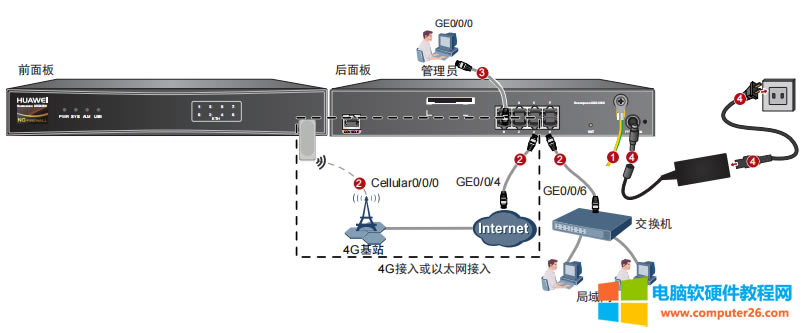 防火墙,默认管理IP地址,及默认帐号和密码。 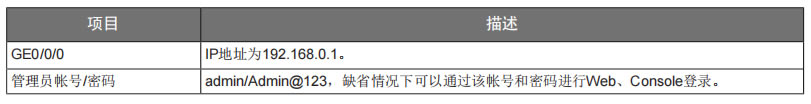 基本的开局配置规划表。 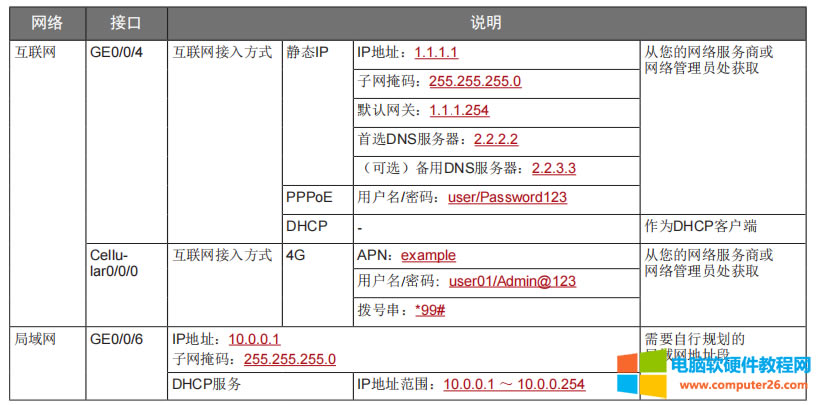 默认密码表。 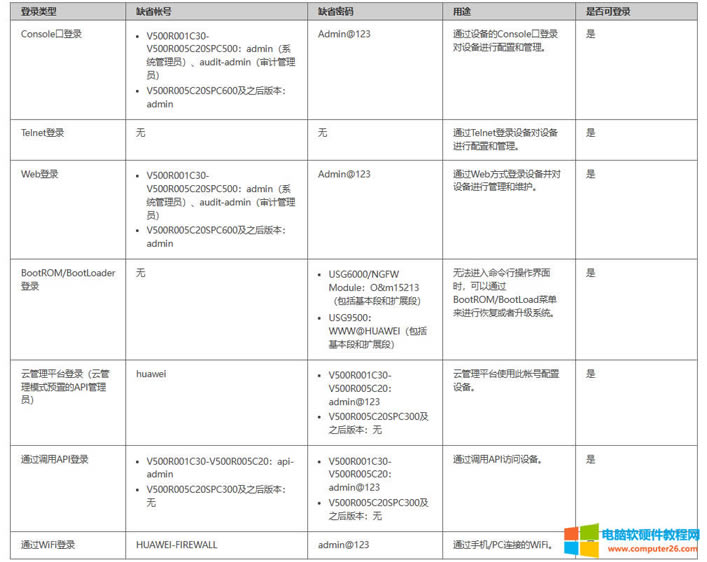 网络拓扑 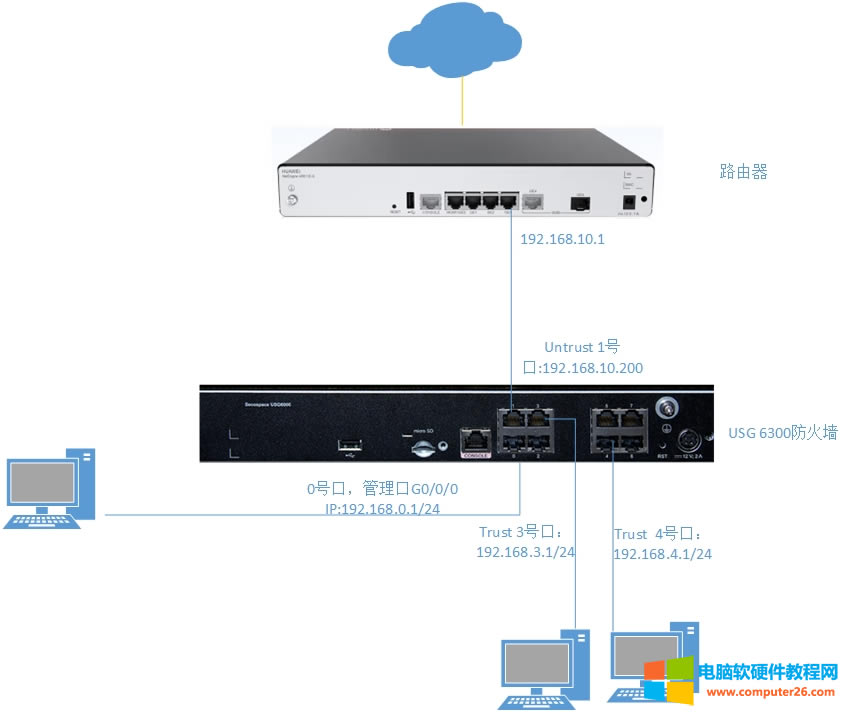 华为防火墙命令配置过程 1.虽说我们使用命令去调试华为的防火墙,但是我们还是需要将web界面打开的,使用web-manager enable,开启防火墙的web界面。 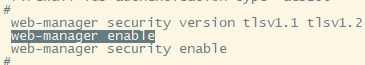 2.查看一下防火墙的现有配置,可以看到当前的G0/0/0号口IP地址是默认的192.168.0.1/24,而且默认开启了http和https登录,允许被ping。 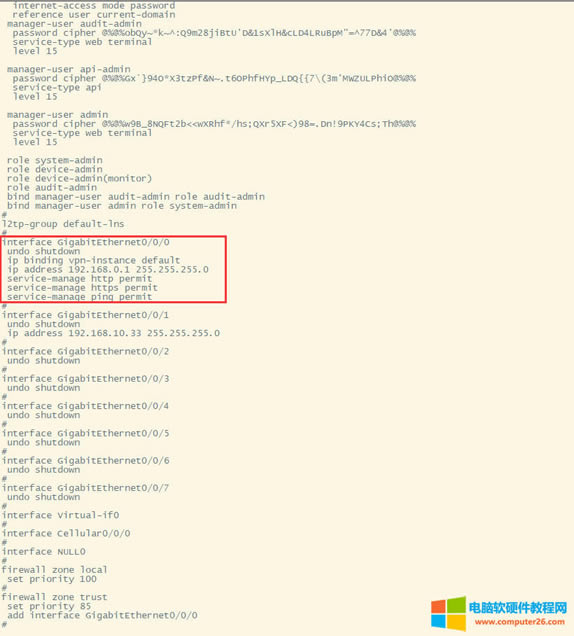 3.在配置命令时,关闭log响应,这样配置起来会更顺畅。使用undo info-center enable,关闭log日志。 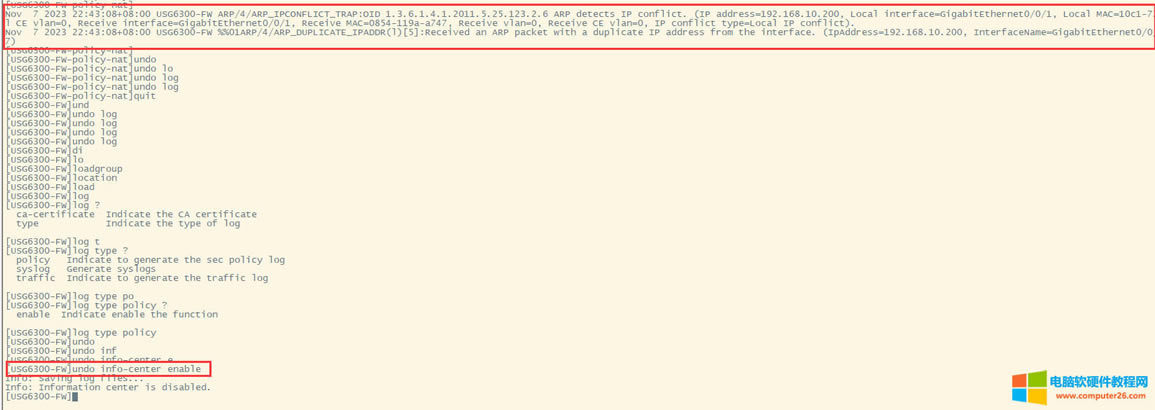 4.划分防火墙的接口区域,因为防火墙是接口分区域的,在之前的文章中已详细讲解防火墙的接口区域划分,请兴趣的可以参考:小白也能看的懂,网络防火墙的入门篇 将G0/0/1划分到外网连接接口,Untrsut。 使用zone untrust进入到untrust区域,然后使用add添加接口到untrust区域。 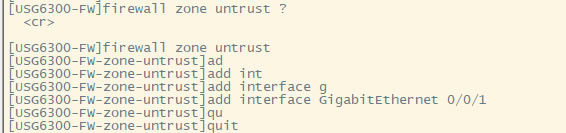 添加完成之后,查看配置,可以看到优先级,默认的配置就是5,可以看到Untrust区域,已经添加了一个接口是G0/0/1。 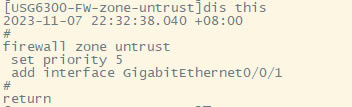 将G0/0/3和G0/0/4添加到Trust区域。 使用zone trust进入到trust区域,然后还是使用add添加接口到信任区域。 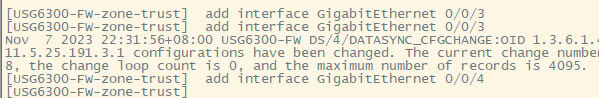 添加完成之后,查看Trust区域配置,可以看到默认的trust区域的优先级是85,里面有一个G0/0/0是默认添加到Trust区域的,还有两个接口是手动添加进来的。 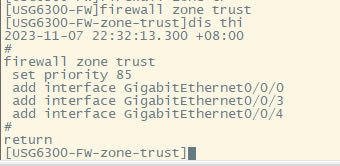 5.DHCP配置 为3网段启用DHCP功能,对于想详细了解DHCP如何配置的,请参考:什么你还不会用命令行,去配置华为防火墙的DHCP服务? ip pool dhcp1 gateway-list 192.168.10.1 192.168.3.1 network 192.168.3.0 mask 255.255.255.0 excluded-ip-address 192.168.3.200 192.168.3.254 lease unlimited dns-list 114.114.114.114 6.配置接口IP地址,公司现在要有两个网段,一个是192.168.3.0/24网段,一个是192.168.4.0/24网段。 外网口配置,untrust区域,接口配置: interface GigabitEthernet0/0/1 undo shutdown ip address 192.168.10.200 255.255.255.0 内网口:trust区域,物理接口配置: 由于是内网口,为了维护方便,直接将所有管理服务允许。 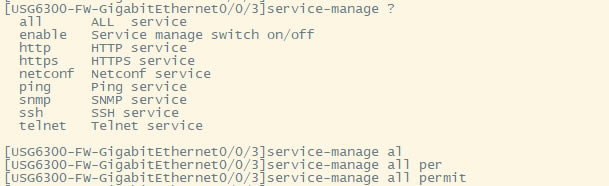 service-manage all permit--允许所有协议登录 配置G0/0/3 IP地址。 interface GigabitEthernet0/0/3 undo shutdown ip address 192.168.3.1 255.255.255.0 service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit service-manage netconf permit dhcp select global--使用的全局DHCP功能。 G0/0/4接口启用的是接口DHCP服务。 interface GigabitEthernet0/0/4 undo shutdown ip address 192.168.4.1 255.255.255.0 dhcp select interface dhcp server excluded-ip-address 192.168.4.2 192.168.4.20 dhcp server dns-list 218.2.135.1 7.配置NAT策略 使用Nat-Policy命令,进入到NAT策略配置中。因为我们这里,只有一个外网口,而且是默认将内网口转发出即可,可以配置easy-IP最简单。将所有流量,都转发到外网口,Untrust接口IP地址。 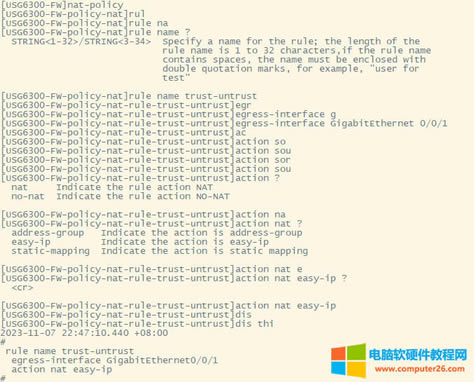 [USG6300-FW]nat-policy [USG6300-FW-policy-nat]rule name trust-untrust---定义一下Nat策略的规则 [USG6300-FW-policy-nat-rule-trust-untrust]egress-interface GigabitEthernet 0/0/1-----定义外网口是G0/0/1接口,英[?i?ɡres]出口、外出 [USG6300-FW-policy-nat-rule-trust-untrust]action nat easy-ip---将内网用户的源地址转换为外网接口的地址 [USG6300-FW-policy-nat-rule-trust-untrust]dis thi--配置完成之后,查看nat配置 2023-11-07 22:47:10.440+08:00 # rule name trust-untrust egress-interface GigabitEthernet0/0/1 action nat easy-ip # return 8.安全区域放行,在防火墙,一共有四个接口区域,untrust、trust、dmz、local,不同区域之前通信,都需要在在防火墙上设置安全策略,允许或禁止不同区域之间的流量访问。 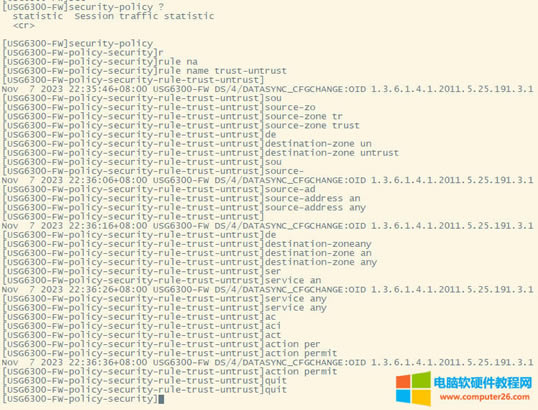 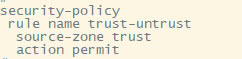 [USG6300-FW]security-policy---进入安全策略 [USG6300-FW-policy-security]rule name trust-untrust---规则名称是trust流量去往untrst [USG6300-FW-policy-security-rule-trust-untrust]source-zone trust---源区域是trust [USG6300-FW-policy-security-rule-trust-untrust]destination-zone untrust---目的区域是untrust [USG6300-FW-policy-security-rule-trust-untrust]source-address any--源地地址是任何IP地址 [USG6300-FW-policy-security-rule-trust-untrust]destination-zone any---目的区域,也是任何地址。 [USG6300-FW-policy-security-rule-trust-untrust]service any---访问的服务也是任何服务 [USG6300-FW-policy-security-rule-trust-untrust]action permit---动作是允许访问 [USG6300-FW-policy-security-rule-trust-untrust]quit---退出 [USG6300-FW-policy-security]dis thi---查看配置 2023-11-07 22:37:23.830+08:00 # security-policy rule name trust-untrust source-zone trust action permit # 9.配置默认路由 ip route-static 0.0.0.0 0.0.0.0 192.168.10.1 此命令用于配置默认路由,将所有未知目的地的流量发送到指定的网关地址(192.168.10.1)。 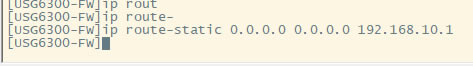 10.这时如你电脑连接到G0/0/3口,会自动获取一个IP地址,可以正常上网。 11、配置导出。 <USG6300-FW>display current-configuration 2023-11-07 22:55:50.970+08:00 !Software Version V500R001C60SPC300 # sysname USG6300-FW # l2tp domain suffix-separator # undo info-center enable # authentication-profile name portal_authen_default # ipsec sha2 compatible enable # undo factory-configuration prohibit # undo telnet server enable undo telnet ipv6 server enable # clock timezone Beijing add 08:00:00 # firewall detect ftp # firewall defend action discard # log type traffic enable log type syslog enable log type policy enable # undo dataflow enable # undo sa force-detection enable # isp name"china mobile"set filename china-mobile.csv isp name"china unicom"set filename china-unicom.csv isp name"china telecom"set filename china-telecom.csv isp name"china educationnet"set filename china-educationnet.csv # user-manage web-authentication security port 8887 password-policy level high user-manage single-sign-on ad user-manage single-sign-on tsm user-manage single-sign-on radius user-manage auto-sync online-user page-setting user-manage security version tlsv1.1 tlsv1.2 # firewall ids authentication type aes256 # web-manager security version tlsv1.1 tlsv1.2 web-manager enable web-manager security enable # firewall dataplane to manageplane application-apperceive default-action drop # dhcp enable # update schedule ips-sdb daily 23:51 update schedule av-sdb daily 23:51 update schedule sa-sdb daily 23:51 update schedule cnc daily 23:51 update schedule file-reputation daily 23:51 # ip vpn-instance default ipv4-family # time-range worktime period-range 08:00:00 to 18:00:00 working-day # ike proposal default encryption-algorithm aes-256 aes-192 aes-128 dh group14 authentication-algorithm sha2-512 sha2-384 sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # web-auth-server default port 50100 # portal-access-profile name default # ip pool dhcp1 gateway-list 192.168.10.1 192.168.3.1 network 192.168.3.0 mask 255.255.255.0 excluded-ip-address 192.168.3.200 192.168.3.254 lease unlimited dns-list 114.114.114.114 # aaa authentication-scheme default authentication-scheme admin_local authentication-scheme admin_radius_local authentication-scheme admin_hwtacacs_local authentication-scheme admin_ad_local authentication-scheme admin_ldap_local authentication-scheme admin_radius authentication-scheme admin_hwtacacs authentication-scheme admin_ad authentication-scheme admin_ldap authorization-scheme default accounting-scheme default domain default service-type internetaccess ssl-vpn l2tp ike internet-access mode password reference user current-domain manager-user audit-admin password cipher % %obQy~*k~^:Q9m28jiBtU'D&1sXlH&cLD4LRuBpM"=^77D&4' % % service-type web terminal level 15 manager-user api-admin password cipher % %Gx`}94O*X3tzPf&N~.t6OPhfHYp_LDQ{{7\ 3m'MWZULPhiO % % service-type api level 15 manager-user adminpassword cipher % %yW9x%WZ z"hm[>T=85R>fsE`hi%w5mvXG<ugJX0*Sc;2sEcf % % service-type web terminal level 15 role system-admin role device-admin role device-admin monitor role audit-admin bind manager-user audit-admin role audit-admin bind manager-user admin role system-admin # interface Vlanif1 dhcp select global # l2tp-group default-lns # interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.0.1 255.255.255.0 service-manage http permit service-manage https permit service-manage ping permit # interface GigabitEthernet0/0/1 undo shutdown ip address 192.168.10.200 255.255.255.0 # interface GigabitEthernet0/0/2 undo shutdown # interface GigabitEthernet0/0/3 undo shutdown ip address 192.168.3.1 255.255.255.0 service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit service-manage netconf permit dhcp select global # interface GigabitEthernet0/0/4 undo shutdown ip address 192.168.4.1 255.255.255.0 dhcp select interface dhcp server excluded-ip-address 192.168.4.2 192.168.4.20 dhcp server dns-list 218.2.135.1 # interface GigabitEthernet0/0/5 undo shutdown # interface GigabitEthernet0/0/6 undo shutdown # interface GigabitEthernet0/0/7 portswitch undo shutdown port link-type access # interface Virtual-if0 # interface Cellular0/0/0 # interface NULL0 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet0/0/3 add interface GigabitEthernet0/0/4 # firewall zone untrust set priority 5 add interface GigabitEthernet0/0/1 # firewall zone dmz set priority 50 # api # ip route-static 0.0.0.0 0.0.0.0 192.168.10.1 # undo ssh server compatible-ssh1x enable # user-interface con 0 authentication-mode aaa user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user-interface vty 16 20 # pki realm default undo crl auto-update enable # sa # location # nat address-group 3test 1 mode pat # multi-interface mode proportion-of-weight # right-manager server-group # agile-network # device-classification device-group pc device-group mobile-terminal device-group undefined-group # user-manage server-sync tsm # security-policy rule name trust-untrust source-zone trust action permit # auth-policy # traffic-policy # policy-based-route # nat-policy rule name trust-untrust egress-interface GigabitEthernet0/0/1 action nat easy-ip # proxy-policy # quota-policy # pcp-policy # dns-transparent-policy mode based-on-multi-interface # rightm-policy # sms # return <USG6300-FW> |
相关文章
上一篇:


